 About CyberAudit-Web Enterprise
About CyberAudit-Web Enterprise

CyberAudit-Web is the software system that manages a CyberLock system. It runs on a server and provides a web or browser based interface. CyberLock, Inc. offers CyberAudit-Web Enterprise both for enterprise level deployments and hosting by approved CyberLock resellers. It can manage CyberLocks, doors connected to the Flex System, and FlashLocks all from one application. CyberAudit-Web Enterprise Basic is available for smaller requirements with fewer feature requirements.
This CyberAudit-Web Enterprise tutorial gives an overview of CyberLock hardware and software. The Getting Started section provides the easiest order of implementation to set-up a system. The first topic is hardware which is the foundation of the system. Afterwards, the focus will be features and capabilities.
CyberLock Hardware
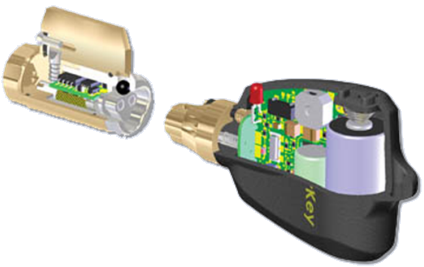
CyberLocks are access control cylinders which have no conventional keyway and can not be picked. These electronic cylinders are the exact dimensions of the mechanical cylinders they replace. They install into the lock hardware with the same ease of the mechanical cylinder and do not change how the lock hardware functions. No wiring or battery is needed at the lock; power is provided by the battery in the CyberKey.
With over 380 cylinder designs, CyberLocks install in interior and exterior doors, padlocks, containers, and cabinets.
CyberLock Cylinder -

The CyberLock cylinder has a circuit board with a micro-processor and memory. Four types of intelligence are stored in the cylinder: Encrypted access codes that ensure only keys within the system work with the lock, the unique ID of the lock cylinder, audit trail records of lock activities, and a list of lost keys.
CyberKeys -
| CyberKeys are highly programmable electronic keys that can not be duplicated. One key can be used to open any of the CyberLocks in the system. Outside entryways, inside doors, cabinets, and padlocks on containers... from beginning to end, only one key is needed. |  |
The key is programmed with the access permissions for that user: What locks they are allowed to open, and on what days and times. In addition, CyberKeys can download audit trails from CyberLocks. User keys can also program locks.
CyberKeys contain four levels of intelligence:
|
 |
The key also houses a clock and the battery that powers the key and locks. There are two types of CyberKey battery: rechargeable and replaceable.
It's important to note that all the data and schedule information is always retained in the key, regardless of the charge state of the battery.
How is it Powered?

|
A replaceable battery inside this key is a standard lithium 3-volt battery that is easily replaced in the field. A single
battery will provide between 2000 and 5000 openings with a maximum life of one year.
When the voltage of the battery is low, the key beeps much in the same way as a smoke alarm. |
| The rechargeable battery in a CyberKey charges in 1 - 3 hours. A single charge will provide up to
500 openings. The rechargeable battery has a five year life.
When the voltage of the battery is low, the key's red LED will flash. If fully depleted, the key will not work until it has been charged and the clock has been reset by communicating with the software via a communicator. |

|
The key supplies power to the cylinder and communications are established. In a fraction of a second, a sequence of events occurs to determine if the key may open the lock.
|
 |
| At the same time, the CyberLock checks the key ID against its list of lost keys.
If the key ID is in the list, the lock denies entry and the key alarms. A denied event is written to the audit trail of the lock and the key. The key is also optionally disabled from working in any other lock. If the key ID is not on the list of lost keys, and the lock and key access codes match, the key gains access. An "Authorized to Open" event is written in the key and the lock audit trails. |
|
 |
 |
| There are additional features that provide an even higher level of security.
For high security areas, CyberLocks can be programmed for either multiple key custody or delayed access. Multiple key custody is used to require 2, 3, or 4 keys to be presented to the lock before a lock will grant access. Delayed access is used in customer applications that require a delay of a few seconds or up to 20 minutes between the time the key is first presented and the time the lock is able to be opened. |
CyberKeys, unlike mechanical keys, can be set to expire regularly, even on a daily basis.
Frequent expiration of keys provides a higher level of overall security with:
|

Expired keys must be reauthorized before they will work again. Communicators are the products key holders use to reauthorize their keys.
To find the balance between security and convenience for the users, there are many types of communicators to choose from:
- Authorizers
- IR Encoders
- USB and ValidiKey Stations
- Flex System Keyports
- Vaults
- Android and iOS Bluetooth phones and tablets

CyberKey Authorizers are durable and ideal for remote locations. They allow users to conveniently renew their expired keys on a daily basis, for a high degree of key control.
The CyberKey Authorizer has two components: the hub and the keyport.
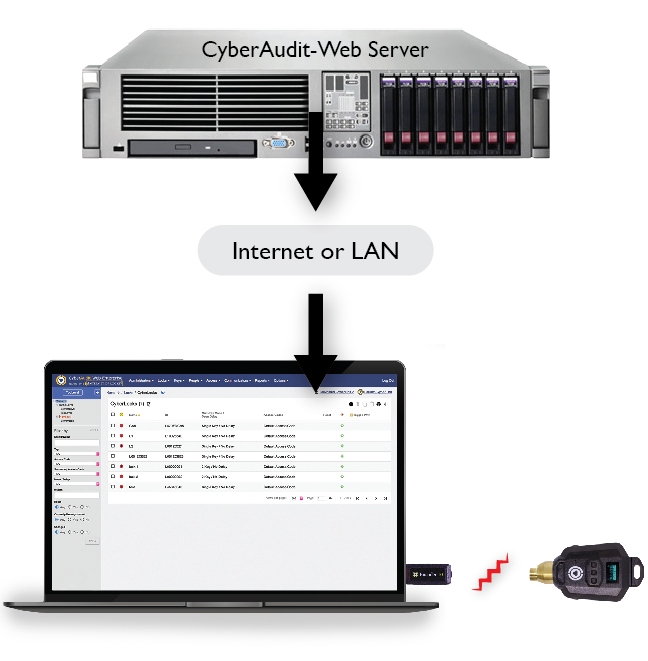
The Authorizer can be used on the Internet or a LAN. It connects to a web service on CyberAudit-Web using SSL over http.

|
The keyport allows users to conveniently update their keys. It is rated for outside
use and attaches to a single electrical box with security screws. It has an
easy-to-read display that leads the key holder through the process of updating their key.
For example, when the key holder arrives, the keyport displays "Ready *". When the key is placed in the keyport, if a PIN is required, the LCD display will request the operator to enter it. Once entered, the display will show downloading, updating, and "Key Ready." |


Gen2 Web Authorizer Keyport and Hub
Introduced in 2019, The CyberKey Web Authorizer 2 is a Generation 2 communicator capable of downloading and programming all Generation 2 CyberKeys as well as all models of CyberKeys described in this manual. It features increased storage (2.5GB vs 60MB) and offers increased network security.
Web Authorizer 2s may be distinguished from the original model Web Authorizer by their black powder coat paint vs the gray powder coat paint of the original units. Also the USB ports on the Web Authorizer 2 are flush mounted, not recessed.
IR Encoder 10
The IR Encoder 10 utilizes a USB connection on a PC.
|
|
The USB Station is attached to a networked computer via USB cable. This Station can be used to charge the CyberKey Rechargeable. |

|
| The CyberLock Flex II System system supports two models of keyports. The Gen2 Web Authorizer Keyport includes a display and keypad for entering a PIN or mission. The Flex System Keyport may be combined with a Keypad Display and also is supported by the original Flex 1 System hub. The flex system combines the functionality of updating a key at the keyport with the possibility to open a door. |

The ValidiKey 2 vault is a key cabinet designed to program and dispense two CyberKeys. The CyberKeys are stored unprogrammed in the cabinet until an approved RFID card is presented. After reading the RFID card, the cabinet checks its local cache and programs the CyberKey with the correct permissions. ValidiKey 2 Vaults store key permissions locally and can continue to dispense and receive CyberKeys if the ValidiKey 2 goes offline.
Other Vaults| CyberKey Vaults store keys unprogrammed in the vault until an approved RFID card is presented or an approved mission number is entered. The vaults below store key permissions locally and can continue to dispense and receive CyberKeys if the they temporarily go off line. | |

|

|
| Weatherized Vaults connect to a Flex System Hub. Each vault holds an individual CyberKey. Up to seven Weatherized Vaults may connect to a hub. | Both the Vault 20S and ValidiKey 20 can hold up to 20 CyberKeys in a locked cabinet. They both have a built-in RFID reader and keypad. The ValidiKey 20 has a built-in display for user feedback. The Vault 20S can output to an external display. |

CyberAuditWeb - Enterprise uses menus to manage a CyberLock system.
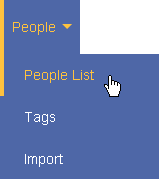
Each menu has submenus that can be selected by hovering over the main menu.
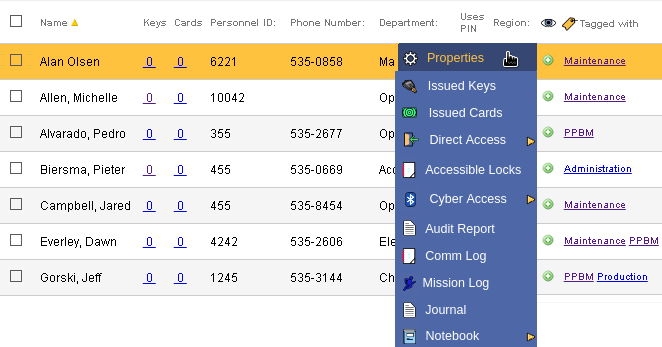
Operations for each window appear by clicking the item. For example, to see the personnel ID and department for Alan Olsen, click on his name. Click "Properties" from the drop down window as seen above.


