Using a CyberLock Programmer II

CyberLock Programmer II enables downloading and programming CyberLocks from an Android device running the CyberAudit Link app or a Windows PC running CyberLink 2. It connects via micro USB cable.
Requirements:
- CyberAudit-Web v9.0.31 or later
- A compatible Android phone or tablet running Android 6.0 or later.
- A USB On-The-Go (OTG) connector that converts to USB type A
- A wireless or mobile network connection to the CyberAudit-Web server
- The CyberAudit Link app downloaded and installed from the Google Play store
-or-
- A Windows PC running Windows 7 or later
- CyberLink 2 version 2.9.2 or later downloaded and installed from the CyberAudit-Web server
|
|
|
|
| After logging in or not, CyberAudit Link will connect to the server then prompt “Ready for Lock”. Insert the reader into a CyberLock and hold firmly to maintain good contact. Follow the CyberAudit Link instructions. If the CyberLock is known to the system, it will download the CyberLock and program it as needed. |

|
|
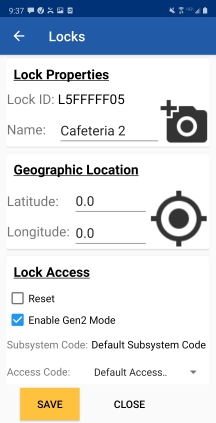
If logged in: When an administrator logs in and they have permission to edit locks, they may perform tasks like naming the lock, adding a photo, and capture geographic coordinates. (The latter option requires the Maps and Location Graphics SEM.) When CyberAudit Link finishes downloading and programming the lock, it will present an edit page for the CyberLock. Editable fields for the app are selected in CyberLock Preferences. |
|
| Tapping the camera icon opens the camera app on the device. (Permissions are required.) Use the camera to take a photo of the CyberLock installation. |
|
| Tap the geo-location icon to capture the geo coordinates of the CyberLock installation. |
|
| Touching an unprogrammed CyberLock that is unknown to the system will automatically add the lock at the same administor node as the login. The user may then name the lock and make other edits. |
|
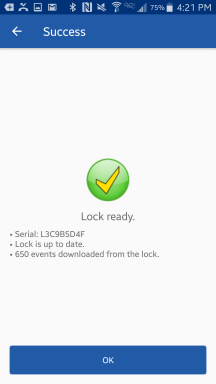
| If not logged in: If logging in is declined, touching a CyberLock in the system will download the CyberLock and program it if needed. Then it shows a success sceen with a summary of information. When not logged in and an unprogrammed CyberLock unknown to the system is contacted, CyberAudit-Link will prompt for a login number. Once entered, that login number will be stored and used for any other such CyberLocks. |
| Additional links |
CyberKey Products
CyberKey Behavior
CyberKey Vaults
Adding a Portable Link
Missions
Audit Trail Events from CyberKeys
Programming CyberLocks with Gen2 Keys

