Templates are a complete set of CyberKey setup instructions. Each subsystem references a "default" template to give to new keys. They encompass nearly all the key details in CyberAudit-Web Enterprise including:
- Expiration
- Expiration Email
- Master Key Mode
- Access permissions granted through the Missions Matrix
- Temporary Access.
- Beeper and other behavior settings
Key Templates differ from keys because:
- They are not issued to a person.
- They do not have a serial number.
- They do not have a change icon.
- They cannot be designated as lost
When a new account is created the default key template has these settings:
- Expiration -> Docking will extend expiration by 7 days
- Expiration email -> None
- Master Key Mode -> Key is not a master key
- No access to locks
- Beeper is enabled
- No beep after expiration
- Solenoid holds open for 1 second
When a CyberKey is first issued to a person, the settings for that key are copied from the settings in the default key template for that subsystem. Alternatively an administrator may create new templates and select one of them when issuing a new CyberKey.
There is also a default template for Missions. They are different from key templates for keys issued to people because missions have a duration rather than an expiration. A mission template may be assigned to a CyberKey Vault.
 Linking Keys and Missions to Templates in Access List Mode
Linking Keys and Missions to Templates in Access List Mode
In access list mode a key or mission may be "linked to" to
the settings of a template. Changes to the template directly apply to the settings for the key or mission.
Conversely, when settings are "copied" from a template, those settings are independent and
changes template won't affect the settings of the other.
Keys and missions "linked to" templates appear in the listing page with a link icon
( ).
).
When access permissions and key behavior can be the same for certain groups of people, there is significant benefit to linking keys and missions to templates. For the administrator making a change to a access permissions or behavior for a group of people, the change only needs to happen in one place. Communicators which cache records such as Web Authorizers, Flex System Hubs, ValidiKey Vaults, and others can greatly reduce load, update time, and network activity by the use of templates. If the key configuration for two keys or missions is linked to a single template, the load is reduced by almost half versus when they are not linked.
Note: A person is limited to one linked mission per template. They may, however have a second mission linked to a different template.
Linking Keys and Missions to Templates in Matrix ModeBecause key templates in Matrix mode don't get access permissions, it is not possible to "link" them to a CyberKey. However people may be granted access to mission templates in the access matrix by selecting "Mission Allowed" in the cell at the intersection of the mission template and the person or people tag.
A person then gains access to the CyberLocks and FlashLocks accessible by the mission in one of two ways:
- RFID Access Card - An RFID Access Card may be linked to a mission template in RFID card properties by setting that template as the default mission.
- Personnel ID + mission number - When a mission number is assigned to a mission template, and a person is granted access to that template in the mission, they may use a keypad on a vault or web authorizer to enter their personnel ID followed by the mission number. Personnel ID is set in people properties. The total number of digits entered may not exceed 8. The number of mission digits expected is set in CyberKey Preferences.
Templates belong to subsystems but they are not automatically visible to all administrator nodes within that subsystem. Visibility may be shared to lower nodes if desired by selecting one more templates from the list, clicking the copy icon from the toolbar, and pasting to additional nodes. If pasting to a node in a different subsystem, a new copy of the template is created. Since templates are inherently associated with lock access permissions, nodes will inherit visibility to any locks referenced in the template. If in access list mode, visibility is also granted to any associated access lists. However if visibility to the template is removed from the node, visibility to the access lists remains in place.
The Default Template in Enterprise BasicMissions are not supported in Enterprise Basic. Instead there is a default template for vaults which appears after assigning an RFID Access Card to a person. This vault template contains the expiration and other behavior rules for all CyberKeys checked out from a vault.
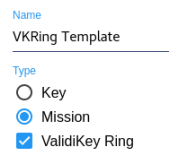
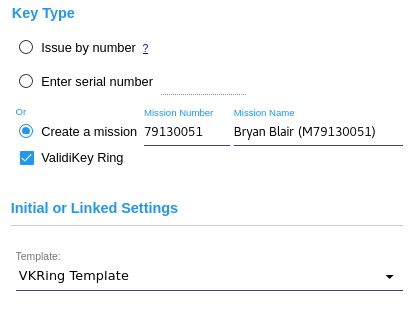
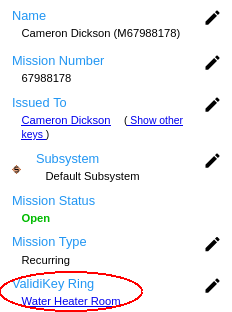
ValidiKey Ring Mission Templates
|
|
|
If ValidiKey Rings will be used in the system, one or more mission templates must be created. A ValidiKey Ring mission template is used to define the initial duration setting and an associated ValidKey Ring or groups for new ValidiKey Ring missions.

