 When a CyberKey Touches a CyberLock
When a CyberKey Touches a CyberLock
The chart below illustrates how the key will behave when it encounters a CyberLock. Use it to help determine when it will or will not open a lock.
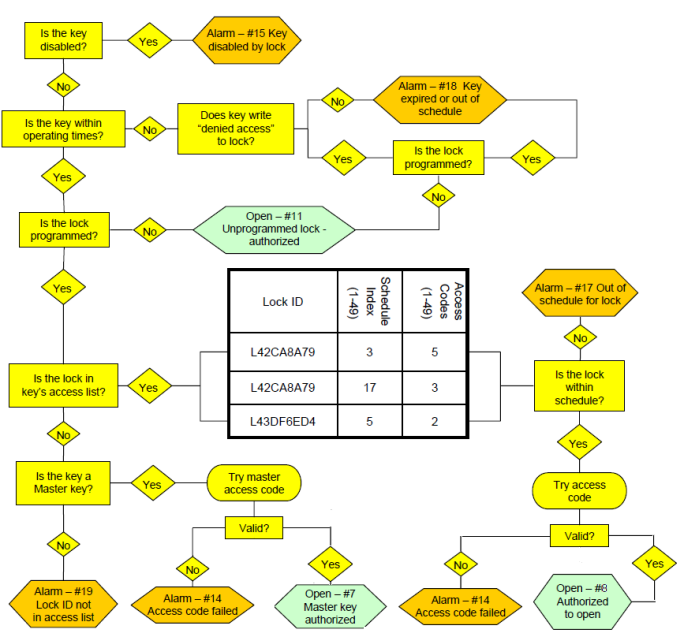
Note: A CyberKey's operating times determine when the key may access locks. Operating times are constrained by:
- Begin date
- Expiration rules
- Schedule by which it opens a lock
When one of the constraints above are in place, a CyberKey validates these rules against its clock. If the clock is not accurate due to loss of power it will deny access to a lock. A CyberKey programmed past its begin date with no expiration, no operating schedule, and full access to a lock has no constraints on its operating times. As such it will open the lock regardless of whether its clock is accurate or not.

