 Access Lists Page
Access Lists Page
An access list matches locks and lock tags with schedules. These reusable lists may then be assigned to a user's CyberKey in order to grant the key holder access to the locks contained in them.
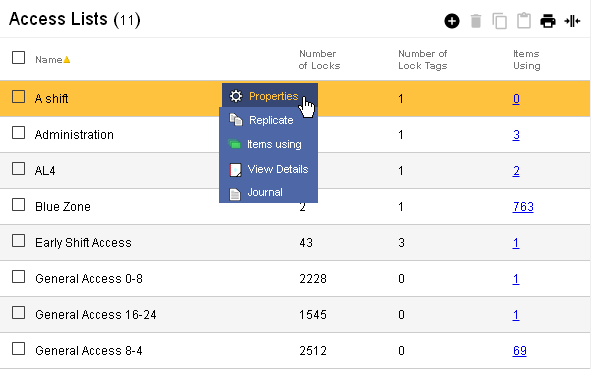
This page lists Access Lists in the system.
Table Fields:
- Name - The identifier given to the Access List
- Number of Locks - A count of the individual locks paired with a schedule
- Number of Lock Tags - A count of the individual lock tags paired with a schedul
- Items Using - A count of the number of CyberKeys, missions, and templates which include this access list in their access permissions hyperlinked to a report of these items.
Operations:
- Page Navigation is controlled by page navigation tools.

They enable browsing to the first and last pages, selecting a page to jump to, or the number of Access Lists per page.  - Use the
toolbar to add a new record, remove a record,
or manage visibility.
- Use the
toolbar to add a new record, remove a record,
or manage visibility.
- Click this button to create a printable report for the current list.
Clicking in a non-linked section of a record will display a drop-down menu of operations:
 Properties - Displays
editable details of the selected access list.
Properties - Displays
editable details of the selected access list.
 Replicate - Creates a copy of
the selected access list. Useful when a new access list would have small differences between itself and
an existing one.
Replicate - Creates a copy of
the selected access list. Useful when a new access list would have small differences between itself and
an existing one.
 Items Using A report of the keys, missions,
and templates which use this access list in their access permissions.
Items Using A report of the keys, missions,
and templates which use this access list in their access permissions.
 View Details - Generates a
report of the individual Locks or tags paired with a schedule.
View Details - Generates a
report of the individual Locks or tags paired with a schedule.
 Journal - Brings up the
Journal of Changes to view a list of edits on the current record.
Journal - Brings up the
Journal of Changes to view a list of edits on the current record.
Related topics:
Creating and Editing an Access List
Holidays
Direct lock access assignments
Temporary access

