 Communication Logs
Communication Logs
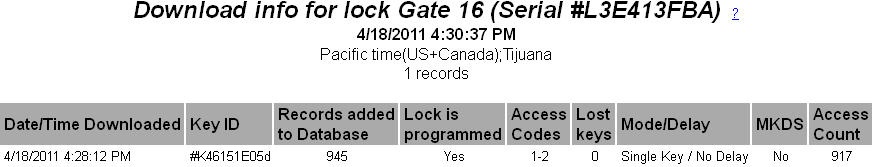
When a CyberLock or CyberPoint is downloaded, a record is kept of the download "session." The session information is viewable from the Communications Log.
- Date and Time Downloaded by CyberAudit-Web - This is the date and time that CyberAudit-Web pulled the audit trail data from the CyberKey, Grand Master, or CyberLock Programmer and recorded it in the system.
- Key - The CyberKey, Grand Master, or CyberLock Programmer that downloaded the lock.
- Records Added to the Database - A CyberLock holds up to the most recent 1100 events in its memory. This
memory is never cleared but the oldest record is overwritten. If the count of records reported in this field is near
1100 events, it is likely the older records have been overwritten with the newer ones. This count will never report
exactly 1100 because:
- Some records in the lock's memory are used to store the date of the resulting date and time.
- Records with identical key IDs, timestamps, and audit trail events are only recorded once in the database.
- Lock is Programmed - Indicates whether the lock has been secured with access codes. If no information was captured when the lock record was written, this field will be blank.
- Access Codes - Indicates which access codes have been
programmed into the lock.
- 1 - The lock contains a system code. This indicates the locks came from a system where manual passwords were entered or secure-random codes were generated.
- 2 - The lock contains an access code. All programmed locks will contain this code.
- 3 - The lock contains a secondary access code. If there is no
If this information was not captured when the lock record was written, this field will be blank.

