 Programming CyberLocks with Generation 2 CyberKeys
Programming CyberLocks with Generation 2 CyberKeys








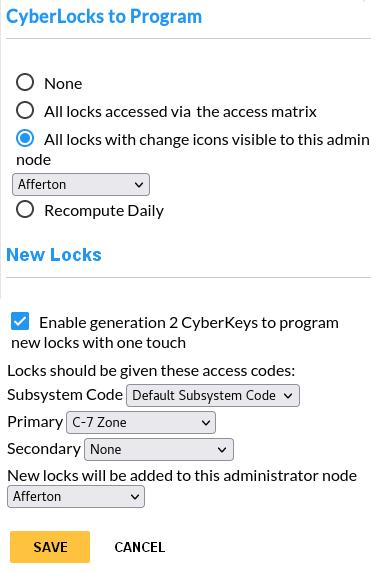
Generation 2 CyberKeys have capabilities to program CyberLocks that exceeds the capabilities of the older Grand Master and CyberLock Programmer Subsystem Keys. Their greatly increased memory enables them to store a list of thousands of locks to program each with potentially a different lock configuration.
Follow the steps below to set up a Generation 2 CyberKey to Program CyberLocks.
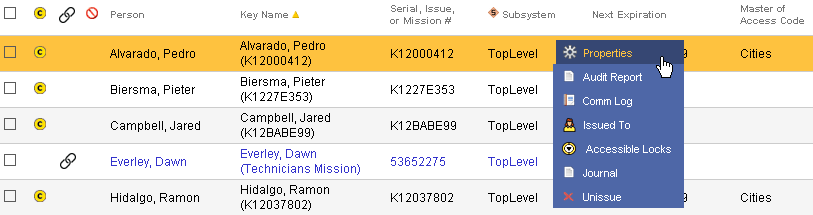
|
|||
|
|||
|
|
||
|
|
||
|

|
||

|
|
||
|
|||
|
|
|||
Additional links
|
CyberAudit Link Using a CyberLock Programmer II CyberKey Products CyberKey Behavior |
Adding a Portable Link Missions Audit Trail Events from CyberKeys CyberKey Vaults |

