 Setting Up and Using Active Directory® or Azure AD to Synchronize People Tags and People
Setting Up and Using Active Directory® or Azure AD to Synchronize People Tags and People
A CyberAudit-Web account can connect to Microsoft Active Directory® or Azure® AD to
people and people tag records.
Users become CyberAudit-Web people ‘linked’ to AD or Azure. Groups become linked people tags.
Linked people and people tags are so indicated with the ‘linked’ icon.

Linked CyberAudit-Web people who are also administrators will log in to CyberAudit-Web using their Active Directory or Azure AD login and password.
On hosted systems, each account on a server can connect to its own instance of Active Directory or Azure AD. The server license must have the Active Directory/Azure AD synchronization SEM (CAW-M05).
Select Global Prefs from the Options menu. Then select Active Directory from the tabbed selector.
|
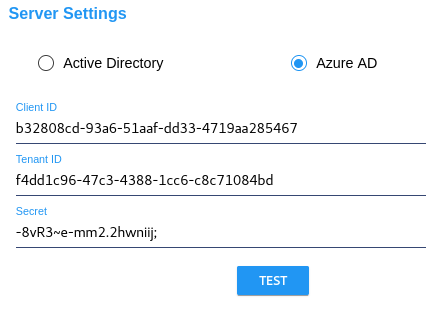
For Azure AD, enter the Client ID, Tenant ID, and Secret for the Azure account.
Setting up Azure AD for a CyberAudit-Web Connection |
|
|
|
|
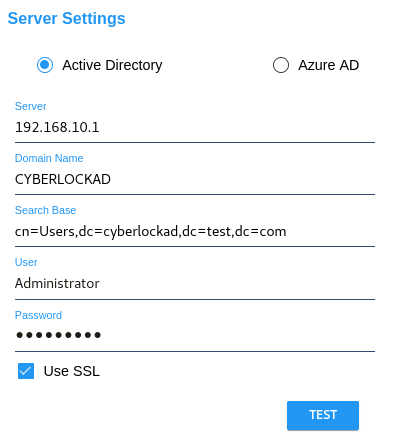
For Active Directory, enter the server URL, domain name, a search base, user, and password.
Optionally check the Use SSL checkbox. The domain name, username, and password are used by CyberAudit-Web to connect to the Active Directory server. The search base in the Active Directory server settings above show we are interested in the ‘Users’ node (cn=Users) with a domain distinguished name of dc=cyberlock, dc=test, dc=com. |
| Click Test to test the connection to Active Directory or Azure. If the test is successful, Active Directory Settings will be added as a tab to the Global Preferences selector. Refer to your Active Directory or Azure documentation to find the required inputs to resolve any connection issues. | |
Systems with an Active Directory server behind a firewall that supports VPN may enable an OpenVPN tunnel to connect to their server. The VPN settings can accept input from either an OpenVPN configuration file or via manual entry. When using a file, click Test to load the file and test the configuration. This will cause CyberAudit-Web to parse the file contents and write them to the inputs as shown in the VPN configuration image below.
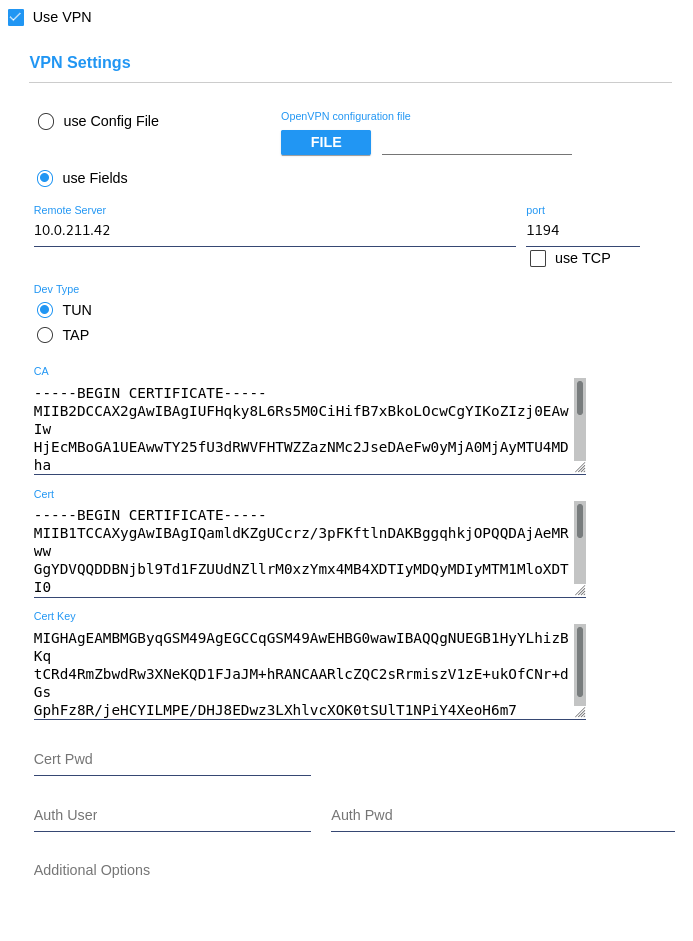
VPN configuration
Selecting Groups and Mapping Attributes to Fields
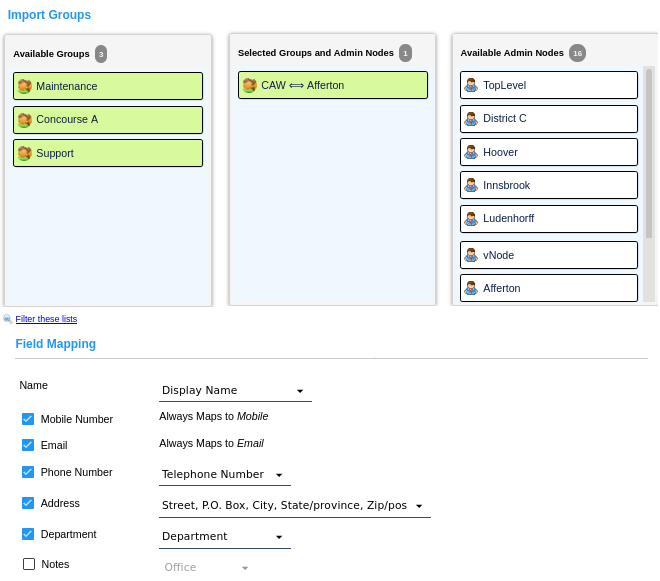
The Active Directory Settings page shows an item chooser populated with the security groups read from the Active Directory/Azure AD server and the administrator nodes in the system. Select the groups to synchronize. Each group will become a "linked" people tag in CyberAudit-Web. Drag and drop an administrator node onto a selected group to set the visibility for that tag.
"Linked" people tags may not be edited in CyberAudit-Web and they are not available for tagging non-linked people.
Fields for linked people records may be also populated from AD or Azure. The fields may be mapped to a fixed set of attributes from the user’s profile. Because the Personnel ID field has constrants in CyberAudit-Web, it is not available to map to an attribute.
After the fields are selected and mapped, clicking the ‘Synchronize’ button connects to the AD or Azure account and synchronizes the users and groups with CAW by adding, updating, or removing the people and groups.
Details about mapping the fields are available from the links below.
Field Mapping with Active Directory
Field Mapping with Azure AD
CyberAudit-Web synchronizes daily with its designated Active Directory or Azure AD server just after midnight. It can also synchronize on demand from the Active Directory Settings page by clicking the Synchronize button.
When Groups and Users are synchronized, any not present are added to existing People tags and People and recorded with their AD or Azure object id. The object id ensures each record is unique. Each subsequent synchronization adds any Groups and Users not already present, updates user attributes, and removes Groups and Users that are no longer present or that don’t match the Groups selected in the Settings page.
Active Directory/Azure AD behavior comparison
The table below illustrates differences in the behavior of Active Directory vs. Azure AD.
| Active Directory | Azure AD | |||
| Administrator Authentication | Uses LDAP or LDAPS to connect to the Active Directory server to authenticate the login and password. | Directs the administrator directly to the Azure AD server to enter their password. Uses OAuth2. | ||
| Available attributes which may be mapped to people record fields. |
|
|
Field Mapping with Active Directory
| The following image shows the possible attributes which may be mapped to each people field when connected to Active Directory. |
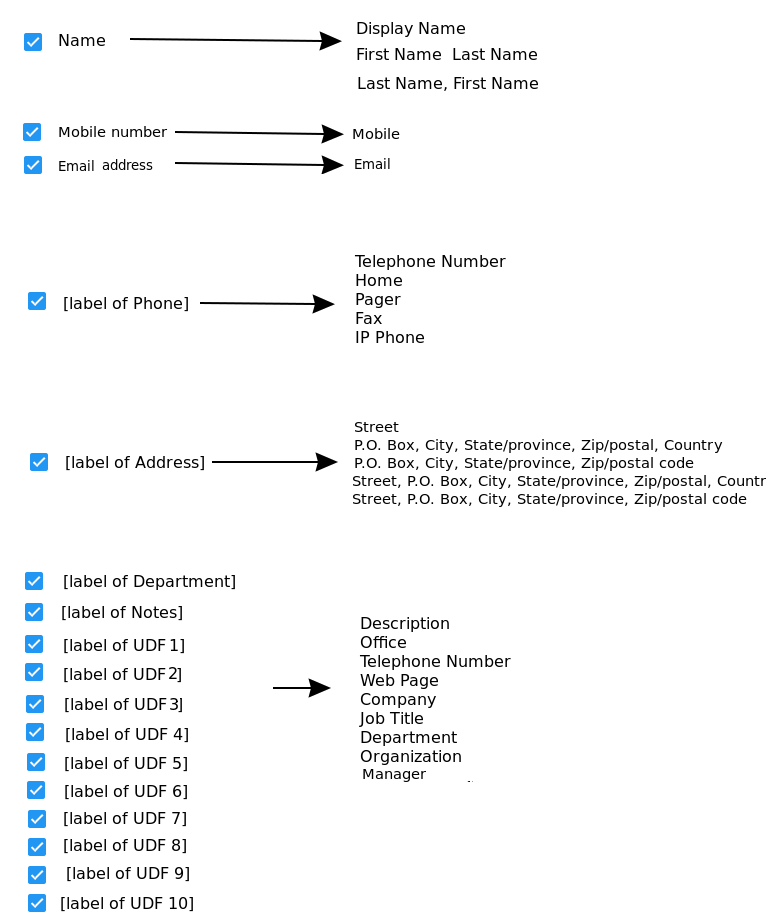
|
| The following image shows the possible attributes which may be mapped to each people field when connected to Azure AD. |
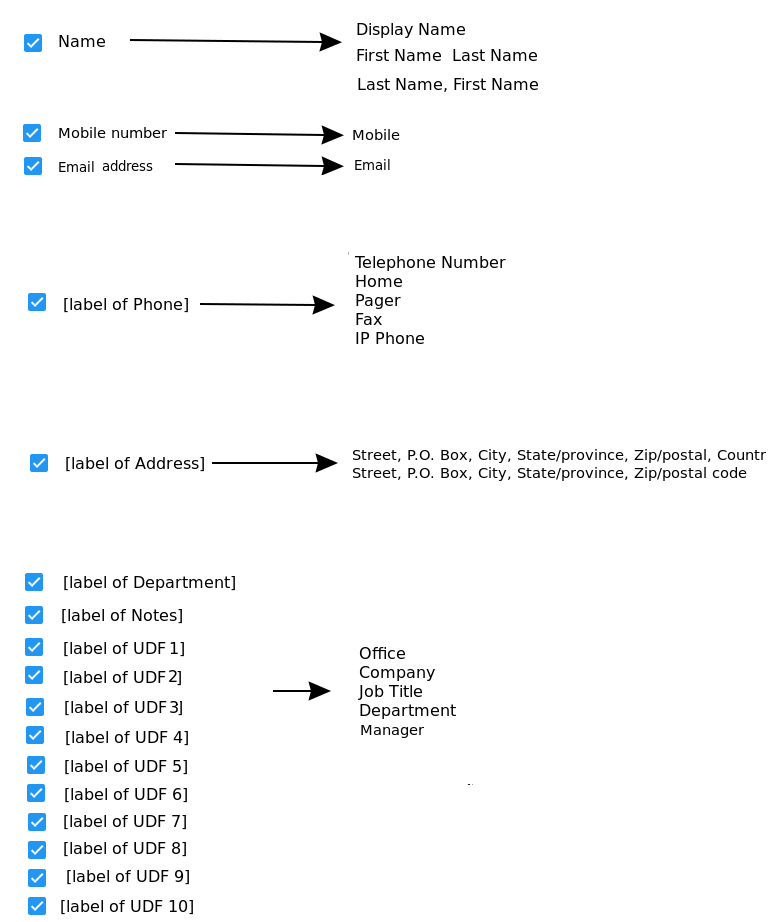
|

