 Create Database
Create Database
|
|
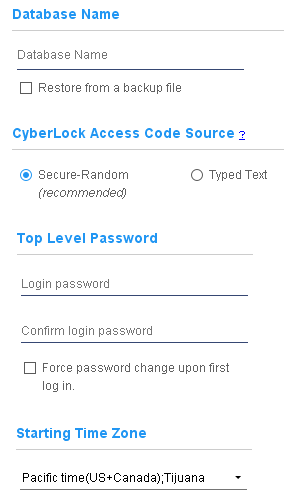
- CyberLock Access Code Source - These are the initial passwords that become the
access codes used by keys to open locks. These access codes may be generated in one of two ways:
- Secure Random - Select this option to create CyberLock access codes that cannot be guessed. The codes are generated randomly using the server's cryptographic strength random number generator. Access codes generated for FlashLock lock tags are always generated as Secure Random codes. Secure Random codes are not visible. It is vital to keep ongoing backups of the CyberAudit-Web database to ensure the system can be recovered in the event of a server hardware failure or data corruption.
- Typed Text -
Select this option to create CyberLock access codes from passwords typed into input forms. This method is weaker than Secure-Random unless the password is very long, very random, and never reused for any other purpose.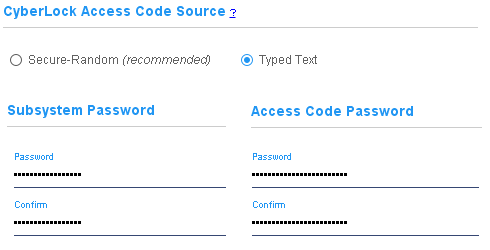
Additional notes about access codes for CyberLocks and FlashLocks:
- For your protection, no record is kept in the server or database of the actual passwords you enter, and there is NO mechanism for recovering lost passwords. There is NO "backdoor" password that allows access to programmed locks.
- If entering Typed Text passwords, select passwords that would be difficult to guess. Use words or phrases that are long. Avoid using personal names, family names, company names, dates of birth, Social Security Numbers, etc.
- Top Level Password - CyberAudit-Web automatically creates a single administrator and login for a new system. It is the "primary" or root login to the system and named "TopLevel" and is assigned to a People record with a name of "TopLevel". Enter a password for this administrator here. Check the Force password change upon first login checkbox if the password you enter should be changed.
- Starting Time Zone - Each communicator in the database as well as each unique administrator operates within a time zone. The Starting Time Zone becomes the default to fill the initial value when a new communicator or administrator is created.


