Global Settings
| Global Settings is divided into several sections accessible by a selector. |
|
|
|
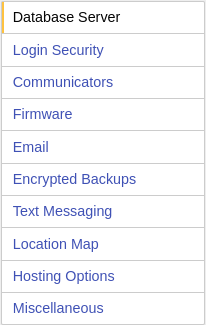
Database Server Login Security Communicator Preferences Firmware Preferences Email Preferences |
Encrypted Backups Text Messaging Location Map Hosting Options Miscellaneous |
|
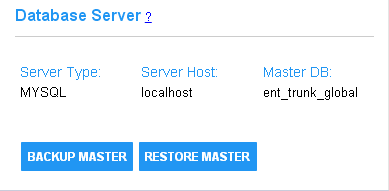
The settings on this page read from the application properties file in the Tomcat root folder.
|
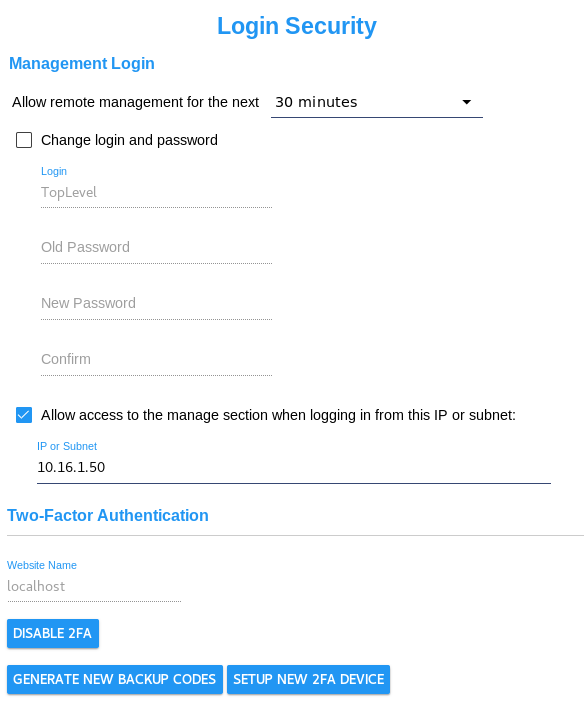
Normally this management system may only be accessed from the server it is running on. Remote administration may be temporarily enabled by logging in from the CyberAudit-Web server console, selecting the Global Settings section and the Login Security tab. Select a time from the drop down menu. A checkbox to enter the Management System will appear on the login page for the time specified on remote browsers. In addition, access to the manage section may be given to browsers sessions that originate from a specific IPV4 ip or subnet. To specify a subnet, put zero in the last octet or the last two octets. Two-Factor Authentication Two-Factor Authentication is a way to make your data more secure by adding an additional step when logging into CyberAudit-Web from a new system. Once Manager enables Two-Factor Authentication, the "TopLevel" user can then enable it for themselves and all other users in their database. Website Name - The Website Name stores the website/hostname that will be displayed on two-factor authentication apps. Note: The Website Name can only be edited while 2FA is disabled. Disable 2FA - This button (which is replaced by " Enable 2FA " when Two-Factor Authentication is not enabled for the user), allows the user to disable 2FA for themselves and all other users. Enable 2FA - This button (which is replaced by " Disable 2FA " when Two-Factor Authentication is enabled for the user), will take the user to the introductory page for 2FA implementation. Generate New Backup Codes - This button is only active if the user has 2FA currently enabled. Clicking this button will take the user to the backup code generation section of the Two-Factor process. Setup New 2FA Device - This button, just like " Generate New Backup Codes ", is only active when 2FA is enabled for this user. Clicking this button with take the user to the final step of the Two-Factor implementation process. |
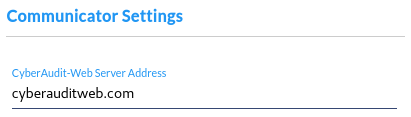
CyberAudit-Web Server Address - The URL or address of the CyberAudit-Web server. This address is used by all communicators in all accounts on the system but may be overridden in the settings for each communicator if desired. In the example above, the full address sent to communicators is https://cyberauditweb.com/CyberAuditWeb. Standard CyberAudit-Web servers are configured to automatically redirect to https and to the CyberAuditWeb folder. |

Newer communicators should enforce valid HTTPS certificates - Just as browsers authenticate valid HTTPS certificates, current communicators for the CyberAudit-Web system can also require basic certificate authentication. Communicators introduced since 2015 are able to enforce this requirement. Certificate authentication includes:
This box should normally be checked. This is especially the case for systems facing the Internet and hosting systems. It may be unchecked on private networks for non-hosting systems where the network is considered secure. Unchecking the box causes this warning to display. 
Enable web wervice for older communicators (SSLv3 port 54443) - Communicators for CyberAudit-Web developed before 2014 cannot support current standards for cryptographic protocols and ciphers. These communicators include: Original WebStations First generation Flex System hubs CyberKey Air First generation Web Authoirizers 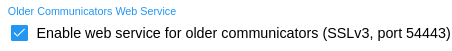
A web service, videx-legacy-ssl serves as a proxy to listen on port 54443 and forward traffic to CyberAudit-Web. If none of the five communicators listed above will be used on this server, this web service may be disabled. |
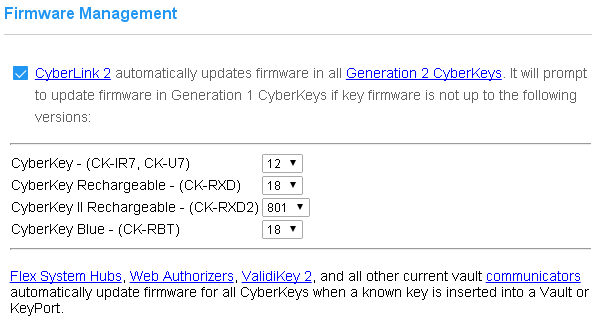
CyberAudit-Web enables updating firmware on all current models of CyberKeys. These include CK-IR7 and CyberKey X CyberKeys and all models of rechargeable CyberKeys. Updates to CyberKey firmware are distributed with updates to CyberAudit-Web. Firmware updates become available for either of two reasons:
|
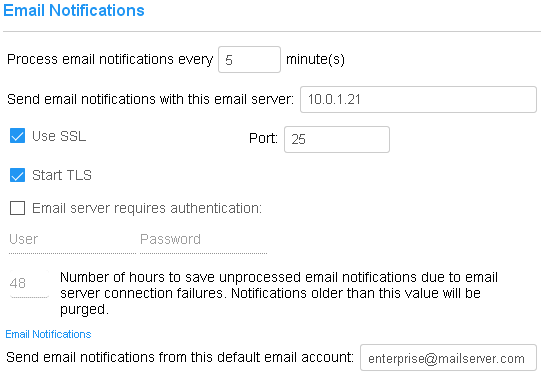
Email Setup - CyberAudit-Web can relay email messages from an email server. These notifications may be used to send low-battery or about to expire warnings to key holders or periodic reports to administrators to help them track access to locks or other activities. This section enables setting up a connection to an email server. Process email notification interval - By default, the CyberAudit-Web periodic task server checks for email notifications every minute. This frequency may be reduced if server load is a concern. Email server: - CyberAudit-Web relays its email notification messages through an email server. Enter the email server's IP Address or DNS name here. By default, the email server must support SMTP on port 25 without secure sockets (TLS). Use SSL - Check to enable an SMTPS connection from the CyberAudit-Web server to the email server. Port - Enter the port number to connect to the email server. Start TLS - Check if the mail server requires the Start TLS protocol. Email server requires authentication: - An email server that operates on the Internet will typically only relay messages from authorized accounts. If so, check this box and enter the user name and password for the account. Check with the email server administrator if an account is needed for CyberAudit-Web. Number of hours to save unprocessed emails - If CyberAudit-Web is unable to successfully send emails due to connection or other failures, it will try again at each processing interval. Once the number of hours has passed since the email was generated, it will no longer try to send. This prevents sending emails where the information is no longer current. Default FROM email account: - Use this field to identify the sender of the email notification. 
When email settings have been saved, click SEND TEST EMAIL to test the settings and ensure emails are being sent. CyberAudit-Web keeps a log of emails sent for the last 30 days. Click VIEW LOG to see all of the email activity including failures. A status of "Success" indicates the message was received by the email server. It does not indicate it was successfully sent to the recipient. Check email server logs to verify it was received by the recipient's inbox. |
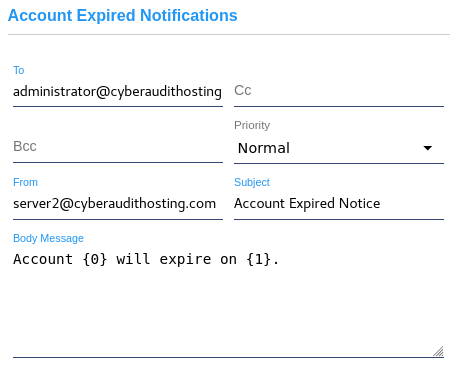
This section sets up the email recipients who will be notified about a pending account expiration. The body message of this email defaults to "Account {0} will expire on {1}. {0} is a placeholder for the name of the account and {1} is a placeholder for the date of expiration. The body message may be modified using these placeholders if desired. |
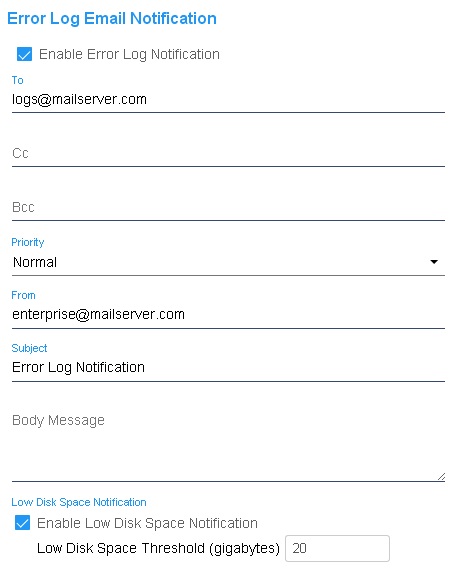
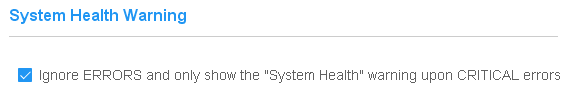
The CyberAudit-Web server can attempt to generate an email notification if an ERROR or CRITICAL ERROR occurs. Typically these notifications should be sent to those who monitor the system, server, and network. Errors - An error that should be monitored but CyberAudit-Web should recover. Critical Errors - Errors that indicate the CyberAudit-Web server is not functioning properly. These errors should be addressed as soon as possible. If the notifications are to be sent to someone who monitors more than one CyberAudit-Web server, the "From" email account or "Subject" should contain something that identifies the server. Error Log Email Notifications can also be configured to send an email if the available disk space falls below a specified threshold. The number supplied is gigabytes of free memory and must be a whole number. The volume checked is the same one as where the java JDK is located. |
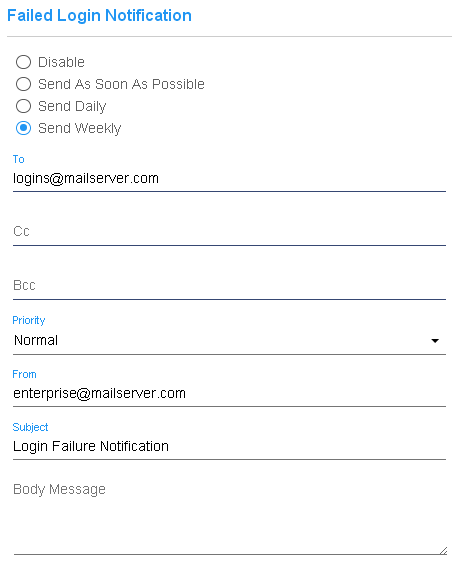
This feature sends an email when there are one or more failures to log in to CyberAudit-Web. |
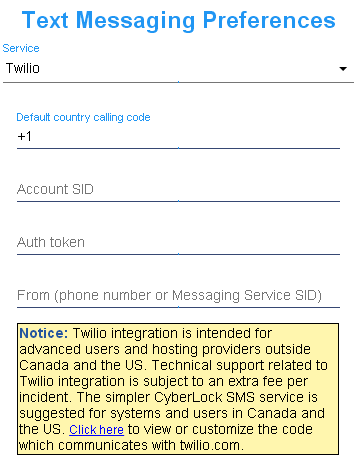
| CyberAudit-Web can connect to a text messaging service to enable sending text messages. They may be sent either as an alternative to or in addition to sending an email. Text messages may be sent for any type of notification in CyberAudit-Web. | |
|
 In key expiration and low battery notification settings the text will be sent to the mobile number in people properties for the owner of the key.  Other types of notifications may be sent to a mobile number entered directly within the properties of the notification. For all notifications, only the subject line is sent in text messages. This is designed to prevent notifications with large amounts of data from being sent via the SMS service. For service in the U.S. and Canada, CyberAudit-Web offers the CyberLock SMS service. It is enabled by purchasing a bundle of text messages which are associated with a CyberAudit-Web license. When the bundle is purchased, just select CyberLock SMS from the drop-down list and click Save. CyberAudit-Web will automatically connect to the SMS service. |
| For advanced users and for systems that serve regions other than Canada and the U.S., CyberAudit-Web also offers a direct connection to the Twilio cloud service to send and receive text messages. | |
| This section allows you to configure Location Map settings. Click here for more information about the Location Map application. | |
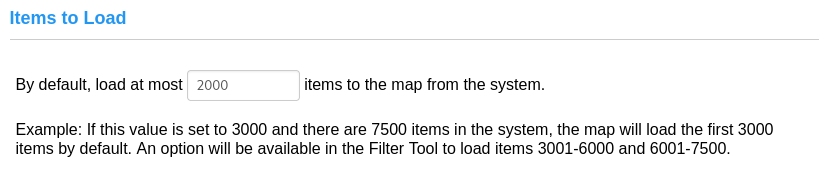
Items to Load: Configure the maximum amount of items to load to the map from the system. This is most applicable for systems with large item counts (3000+). Example: If this value is set to 3000 and there are 7500 items in the system, the map will load the first 3000 items by default. An option will be available in the Filter Tool to load items 3001-6000 and 6001-7500. |
|
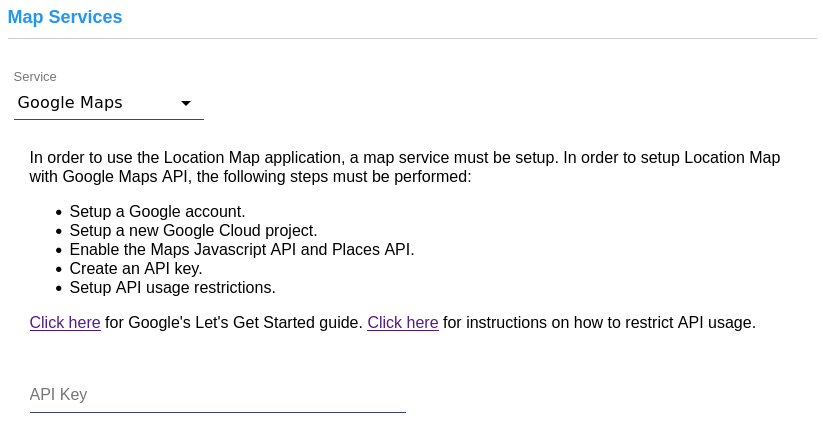
Map Services: This section is used to configure the Map Service API that the system will use. In order to use the Location Map application, a service must be set-up. Follow the instructions after selecting a service and configure the API Key input and other values as needed. Click here for additional Location Map set-up instructions. |
|
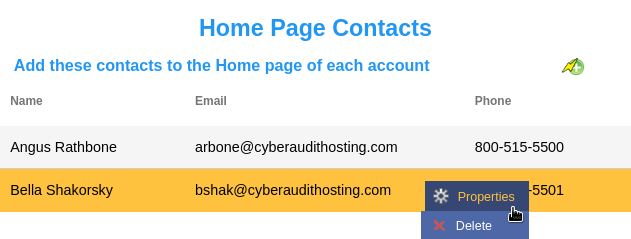
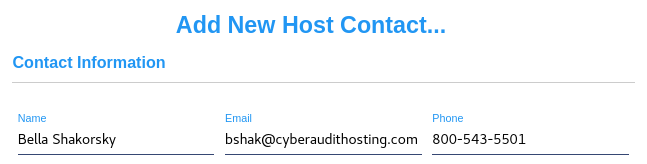
Managers of a system that hosts CyberAudit-Web accounts can use this page to enter contact information which will appear in the list of contacts on the bottom of the Home page of every account. Names entered here will appear before those added in the Home Page Contacts in Global Preferences of each account. Click the  icon to add a new contact or use the
Click Menu to modify or delete it. icon to add a new contact or use the
Click Menu to modify or delete it.
|
|
|
| When errors occur in the CyberAudit-Web system, an exclamation icon is displayed in the upper right corner of each main section next to the Logout button. |
|
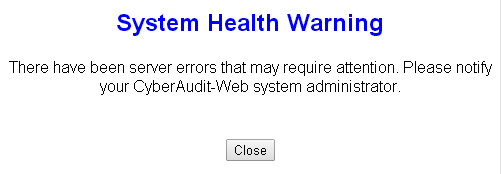
| When an administrator clicks on the exclamation icon this pop-up appears... | |
|
|
|
...telling the user to notify the system administrator that there is an error.
On non-hosted systems, clicking on the exclamation icon brings up the Server Logs page. There are three levels of errors:
|
|
|
|
|
|
|
|
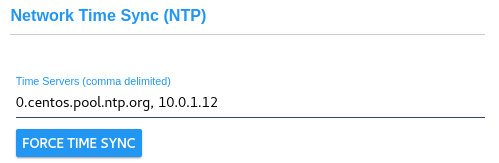
The Network Time Protocol service (ntpd) helps to ensure your CyberAudit-Web server
clock is synchronized with Internet time. A default NTP server, 0.centos.pool.ntp.org
is used when NTP is enabled. If the server will not connect to the Internet,
enter an IP or DNS name where the CyberAudit-Web server may synchronize its time. When the page is in edit mode, click FORCE TIME SYNC to force the server to synchronize its time right away. |
|
|
|
|
|
|
| SSH enables command line access from a remote computer. Much of the administration for a CAW server requires access to the command line. Be sure you have other command line access to the server if you choose to disable SSH. | |